CyberCheck Plus

Automated Cyber Supply Chain Risk Monitoring & AI Powered Cyber Recommendations
![AdobeStock_552074522 (1) [Converted]](https://sparkcllc.com/wp-content/uploads/2025/08/AdobeStock_552074522-1-Converted-150x150.png)
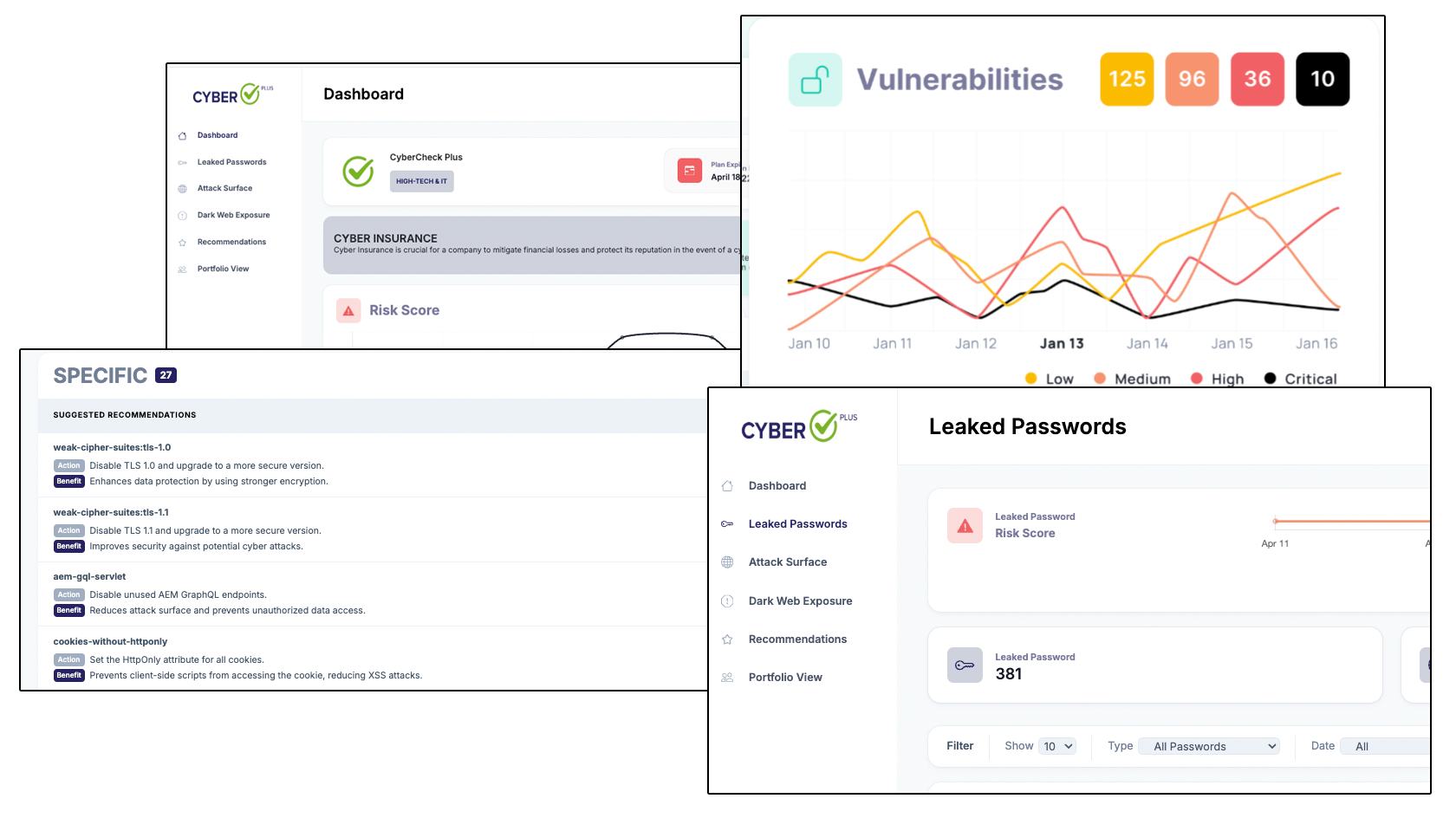
Passwords & Dark Web Monitoring

Attack Surface Management

Vulnerability Scanner

AI Recommendations
Advanced Vulnerability Scanner
Our supply chain risk scanner sends targeted requests based on pre-built templates, delivering zero false positives and enabling rapid assessments across large vendor ecosystems. We support scanning for key protocols including TCP, DNS, HTTP, and file services, ensuring broad visibility across supplier and third-party environments. With a flexible templating engine, critical security checks are automatically aligned to supply chain assurance requirements.
We maintain a dedicated repository containing diverse vulnerability templates contributed by more than 200 security researchers and engineers. These templates reflect the latest exploits, CVEs, and supply chain attack methods, ensuring continuous coverage against evolving risks.
Leaked credentials were the root cause of 22% of cyber breaches.
Monitor leaked passwords and credentials to strengthen your supply chain resilience.
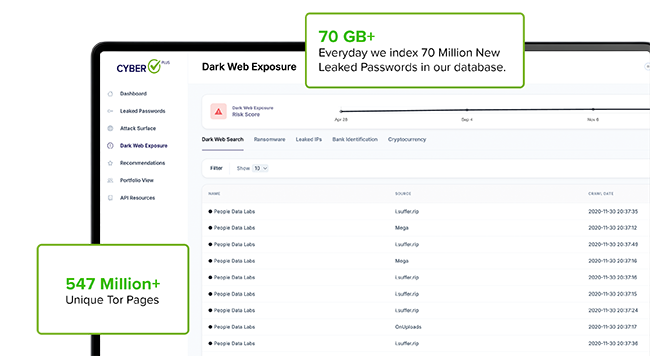
Unmatched Darknet Content Discovery
We Access and Analyze the Largest Commercial Dark Net Database
Compromised supplier and third-party data on the darknet is often uploaded and deleted within days, leaving blind spots in risk monitoring. With CyberCheck Plus’s database, clients can review historical darknet exposures tied to their vendors and partners—long after competitors’ tools lose visibility. Unlike point-in-time searches, CyberCheck Plus continuously crawls and indexes millions of internet and darknet pages daily, building the industry’s largest searchable repository. This enables organizations to proactively identify hidden breaches, credential leaks, or sensitive data exposures across their entire cybersecurity supply chain.
Automated
Exhaustive
Exhaustive Data Sources
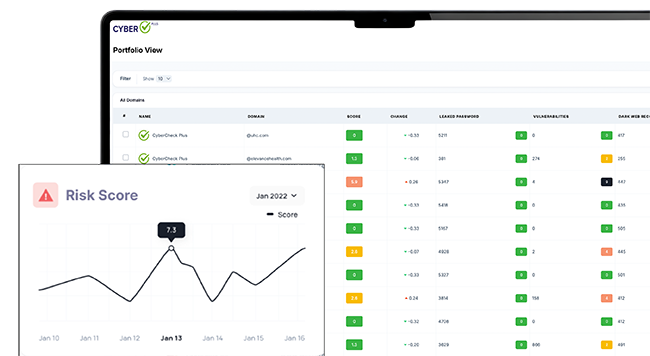
Advanced Supply Chain Risk Rating
Solutions We Offer
To strengthen supply chain resilience, we automate the collection of critical intelligence that adversaries typically map when targeting suppliers and third parties. By viewing the ecosystem from a hacker’s perspective, clients gain a comprehensive understanding of vulnerabilities across their supply chain. This visibility enables proactive identification and mitigation of risks before they can be exploited by malicious actors, reducing the likelihood of cascading breaches through interconnected partners and vendors.

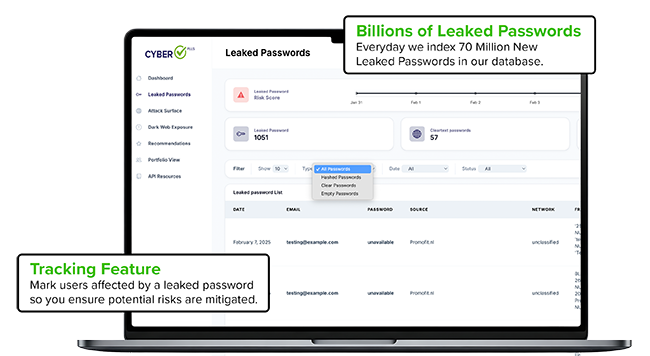
Leaked Passwords
We combine the power of AI with expert human analysts to proactively identify and assess compromised credentials and exposed logins across suppliers, vendors, and third-party partners. This approach ensures early detection of vulnerabilities that could cascade through the supply chain, reducing the likelihood of your organization becoming a prime target for cybercriminals.
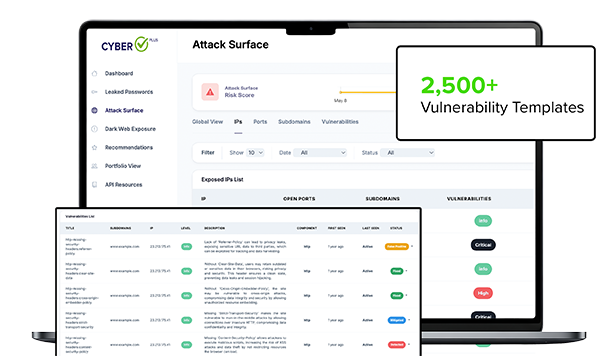
Attack Surface Management
Know the external Internet surface area of any company through a simple web-based interface. Check the status of all Internet-facing assets to get the most accurate picture when it comes to third-parties or your own network.
Vulnerability Scanner
Our scanner proactively evaluates supplier and third-party environments by sending template-based requests that ensure zero false positives while delivering rapid, scalable scanning across large networks of hosts. This enables organizations to quickly validate the security posture of their extended supply chain with accuracy and efficiency.
Dark Web Data Leakage
Identify exposed supplier and third-party credentials, ransomware-related data leaks, illicit machine access sales, and customer PII listings tied to your organization or partners across IRC channels, underground forums, and criminal marketplaces—helping to uncover and mitigate risks before they propagate through the cybersecurity supply chain.
AI Recommendations
Powered by our Machine Learning model and OpenAI, organizations receive personalized cybersecurity recommendations and clear, actionable remediation plans tailored to their unique supply chain risk profile—helping mitigate vulnerabilities across vendors, partners, and third-party ecosystems.


Gain Visibility and Increase Cyber Resilience across your supply chain.
Interested to Know More?
Cypherleak’s platform automatically, anonymously, and continuously collects, indexes, and ranks darknet data from various sources, including Tor, I2P, and ZeroNet. This comprehensive approach ensures access to the most current and relevant information.
Yes, CyberCheck Plus’s tools enable organizations to detect compromised data on the darknet, allowing for swift identification of security gaps and mitigation of potential damage before the data is misused.
Absolutely. CyberCheck Plus’s platform is designed to provide secure access to darknet data without exposing our clients or supply chain network or systems to potential threats. Our services ensure that our interactions with darknet data are conducted safely and anonymously.
CyberCheck Plus’s Attack Surface Intelligence is a comprehensive solution that strengthens supply chain cybersecurity by enhancing visibility into third-party and vendor assets, prioritizing exposures for remediation, and enforcing consistent security controls. It enables automated, continuous discovery of external assets across suppliers and partners, attributing them back to your organization for real-time inventory management, and provides detailed asset intelligence for rapid investigations—helping reduce systemic risks across the entire supply chain ecosystem
While traditional scanners focus only on internal systems, CyberCheck Plus’s Attack Surface Intelligence delivers an external, supply chain–wide perspective. It continuously monitors internet-facing assets across suppliers, vendors, and third parties, uncovering exposures such as misconfigurations and shadow IT, providing critical insights that complement internal assessments and strengthen overall supply chain resilience.
Cyber Check Plus’s vulnerability scanning engine is a fast, customizable vulnerability scanner leveraging a templating library for applications, cloud infrastructure, and networks, aiding in vulnerability identification and remediation.
Web Application Scanning: Identifies web vulnerabilities with community-powered templates. Infrastructure Auditing: Assesses configurations, open ports, and services. API Testing: Evaluates APIs for vulnerabilities. CI/CD Integration: Enables seamless security checks within deployment pipelines. Cloud & Database Scanning: Examines cloud environments and databases for misconfigurations and vulnerabilities.
The Dark Web is a hidden universe contained within the “Deep Web”- a sublayer of the Internet that is hidden from conventional search engines. Search engines like Google, BING and Yahoo only search .04% of the indexed or “surface” Internet. The other 99.96% of the Web consists of databases, private academic and government networks, and the Dark Web. The Dark Web is estimated to be 550 times larger than the surface Web and growing. Because you can operate anonymously, the Dark Web holds a wealth of stolen data and illegal activity.
Our service is designed to help both public and private sector organizations detect and mitigate cyber threats that leverage stolen email addresses and passwords. Cypherleak leverages a combination of human and artificial intelligence that scours botnets, criminal chat rooms, blogs, Websites and bulletin boards, Peer to Peer networks, forums, private networks, and other blackmarket sites 24/7, 365 days a year to identify stolen credentials and other personally identifiable information (PII).
Cyber Check Plus focuses on cyber threats that specifically impact our clients’ extended supply chain environments. We continuously monitor the Dark Web and underground criminal forums for exposed credentials tied to client and third-party domains, targeting top-level email domains of suppliers, vendors, and partners. When compromised credentials are detected, they are harvested and analyzed to provide early warning of supply chain risks. Beyond open sources like Pastebin, our intelligence extends into hard-to-access communities that require credibility or membership to enter. To achieve this, we monitor over 500 IRC channels, 600,000 private websites, 600 social feeds, and execute 10,000 refined queries daily—providing unmatched visibility into hidden risks across the cybersecurity supply chain.
This means the password was published as “hashed” (still encrypted). Hundreds of encryption dictionaries are readily available on the Web, and it’s not uncommon for these passwords to be “cracked” or decrypted and available on multiple 3rd party websites.
Employees often recycle passwords throughout their work and personal networks. If your internal requirement is to have a capital letter and special character, it’s common practice for employees to use a password they are familiar with, and add a capital letter and exclamation mark. (Example: Exposed Password: cowboys, Variation: Cowboys!, Cowboys1, Cowboys! 1, and so on.) Knowing this, hackers will. run scripts using metasploit frameworks (hacking and pentesting tools) to “brute force” their way into an unsuspecting system.
Dark Web Chatroom: Compromised data discovered in a hidden IRC; Hacking Site: Compromised data exposed on a hacked Website or data dump site; Hidden Theft Forum: Compromised data published within a hacking forum or community; P2P File Leak: Compromised data leaked from a Peer-to-Peer file sharing program or network; Social Media Post: Compromised data posted on a social media platform; C2 Server/Malware: Compromised data harvested through botnets or on a command and control (C2) server.